
XIOGUARD
THE ULTIMATE MANAGED SECURITY SERVICE FOR 360 DEGREE CYBERSECURITY COVERAGE
Comprehensive Packages Starting at $1000 per month

User and Entity
Behavior Analytics
(UEBA)
Automated
Threat-Hunting
(ATH)
Network Traffic
Analysis
(NTA)
AI and ML
Powered
Event Coordination
Precision
Automated
Response
Integrated Security
Orchestration, Automation,
and Response (SOAR)
XioGuard uses a single unified view of your environment with a highly specialized security operations platform that is automatically and constantly discovering new assets, profiling users, and identifying their behavior and risk.
XioGuard systems will automatically hunt threats by leveraging the library of cybersecurity apps and by querying any field in Interflow records taking automated action in minutes rather than hours.
XioGuard collects the right data with accurate cybersecurity analysis utilizing 360 degree visibility for advanced detection, correlation, and automated response.
The XioGuard advanced AI Engine leverages the industry-leading machine learning algorithms for different scenarios and builds with strong security knowledge to detect sophisticated threats.
XioGuard launches calculated and precise automatic responses through direct NGFW, EDR and Active Directory integration, through SOAR integration or through incumbent SIEM systems.
The XioGuard Network Detection Response (NDR) allows for both automatic and manual responses implemented through the integrated SOAR.
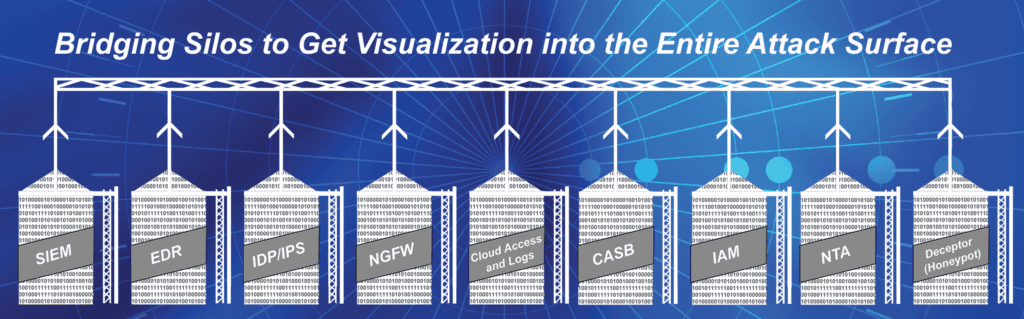
XioGuard employs an open XDR Next-Generation SIEM platform for 360-degree detection and response by ingesting data from all tools, correlating data across the entire attack surface, delivering high-fidelity detections, and responding to threats automatically through AI/ML. The unified platform ingests data from existing security tools to deliver 360-degree visibility and response capabilities across the entire attack surface. This AI-powered platform also learns as it works over time to become faster and more sophisticated at detecting, correlating, and responding to incidents.
User and Entity Behavior Analytics
Day-to-Day In-Depth Network Threat Detection and Anomalous Activity Monitoring
Prioritized, Valid Security Incidents with Correlated and Raw Details
Automatic Threat Hunting
Event Log and Network Flow Data Consolidation
Real-Time and Long-Term Search with Web-Like Query and Iterative Filtering
Network Traffic Analysis
Comprehensive, Extensible Analytics
Compliance and Standards-Based Reports
Artificial Intelligence and Machine Learning (AIML) Powered Event Coordination
Network, Virtualization, and Application Intelligence
Log Management
Precision Automated Response
File and Registry Access Monitoring
Event Alerting
Integrated Security Orchestration, Automation, and Response (SOAR)
Real-Time and Historical Cross-Correlation
Incident Analysis Assistance
Often, indicators of compromise (IOCs) go unnoticed or unresolved in your systems environment. XioGuard helps identify and resolve these IOCs quickly before it’s too late:

- Suspicious entries in system or network accounting, or logs
- Discrepancies between logs
- Repetitive unsuccessful login attempts within a short time interval
- Unexplained new user accounts
- Unexplained new files or unfamiliar file names
- Unexplained modifications to file lengths and/or dates, especially in system files
- Unexplained attempts to write to system files or changes in system files
- Unexplained modification or deletion of data
- Denial/disruption of service or inability of one or more users to log in to an account
- System crashes
- Poor system performance of dedicated servers
- Operation of a program or sniffer device used to capture network traffic
- Unusual time of usage (e.g., user login during unusual times)
- Unusual system resource consumption. (High CPU usage)
- Last login (or usage) for a user account does not correspond to the actual last time the user used the account
- Unusual usage patterns (e.g., a user account associated with a user in Finance is being used to log into an HR database)
- Unauthorized changes to user permission or access

WHAT DOES XIOGUARD COST?
$1000 per month (up to 10 GBs of logs per day)
Package can be upgraded to include:
-
-
-
Intrusion, Detection to Malware Command and Control Detection/Analysis
-
Sandboxing
-
Deceptor
-
-
We gathered select industry articles that may be of interest to you in your search for the best Managed Security Service options.
Managed Security Services
The complexity of securing today’s enterprise has become even more daunting, businesses with large and small IT staffs are looking to Managed Security Service Providers (MSSPs) to shift risk from their IT departments into the hands of dedicated security professionals.
Memo from the White House: What We Urge You To Do To Protect Against The Threat Of Ransomware
Read the White House memo urging corporate executives and business leaders to take immediate cybersecurity steps and lists the five best practices for safeguarding against ransomware attacks.
New Ransomware Strategies for 2021
How to detect breaches early through lateral movement. Short discussion followed by a 5 minute demo
Global Threat Landscape Report
The latest Global Threat Landscape Report represents the collective intelligence of FortiGuard Labs. Its data is drawn from Fortinet’s vast array of sensors collecting billions of threat events observed around the world and processed using one of the world’s most advanced AI systems during the second half of 2020.
MSSP Adoption: Managed Security Services Demand Surges in UK
UK businesses will increasingly outsource cybersecurity to managed security services providers (MSSPs), new NTT research findings & forecasts suggest. by Dan Kobialka • Oct 30, 2017 A lack of cybersecurity skills and a need for advanced technology is leading many UK businesses to partner with managed security services providers (MSSPs), according to a report from security, risk and compliance services company NTT Security.Key findings from the NTT Security “Risk: Value 2017” report,…
What does stolen data cost [per second]
Trading in intellectual property and personal data is so widespread that someone invented a calculator that can estimate the potential harm to your own business.Nearly 5 million data records are lost or stolen worldwide every single day, according to the Breach Level Index. That’s a staggering 58 records every second. High-profile data breaches hit the headlines with worrying frequency. Just last year there were notable incidents at Equifax, Verizon, and Kmart, to name just the three biggest…
The Benefits Of Managed Security Services For Online Businesses
Managed Security Service Providers (MSSPs) are third party providers of expert security services. They work by offering security services either in-house or remotely, overseeing everything from setting up security processes to ensuring smooth day-to-day running. Online businesses need to be on top of their security to prevent data hacks and breaches and using an MSSP creates an easy and reliable way to do so. There are many reasons why every online business, from e-commerce to retail, can be…
Evolution of Managed Security Services in the Future
The need to protect delicate information and sensitive data as well as thwart organized cyber attacks has driven industries across several verticals—including banking, manufacturing, healthcare, and retail—to employ Managed Security Services (MSS). MSS are third-party security service providers that remotely monitor and manage the network infrastructure of such organizations. While most organizations today manage IT security in-house, a rising trend among IT professions is to partner with an …
Do Not Underestimate the Challenge of Securing SD-WAN
Historically, the branch office of an organization was the red-headed stepchild of the network. Locally cached data tended to be out of date and connections to the central data center were often slow and unreliable. This was fine when interactions with customers and databases were slow, and the number of devices connected to the branch network was limited. But digital transformation has changed all of that.Today, transactions, workflows, applications, and data requests at the branch need to…
5G Security Transformation: Why Businesses Need to Prepare Now
New 5G networks will offer faster speeds, lower latency and more reliable connections, launching a new era of wireless networking and connected solutions. As a result, it is projected that the number of 5G users will grow to more than a billion by 2023. Many of these customers will take advantage of 5G speeds to deploy new Internet of Things and connected devices that employ edge-based computing to process huge volumes of data. To address this explosive rate of growth and innovation, business…
How to Select a Managed Security Service Provider (MSSP)
Credit: ID 17575170 © Hannu Viitanen | Dreamstime.com During a recent trip to the Gartner Security and Risk Summit in Sydney, I attended a session on how to select a Managed Security Service Provider (MSSP), which had some really good points on what customers need to understand when evaluating an MSSP. Traditionally, Managed Security Service Providers (MSSPs) have offered security services such as managed anti-virus, managed firewall, and web filtering which consist of conducting tas…
5 Reasons to Purchase Cybersecurity From a VAR
The digital business model requires organizations to adopt a new approach to securing data and networks. At the same time, technology and networks are evolving, making security more complex.One of the biggest challenges is the sheer number of security products and vendors inside an organization. According to our technology partner Fortinet, Some larger financial enterprises; for example, use products from as many as 40 or more vendors to secure their networks.All these products — firewa…
Xiologix Recognized as a 2020 Top Provider!
“CRN’s Managed Service Provider 500 list recognizes the top technology providers and consultants whose forward-thinking approach to providing managed services is changing the landscape of the IT channel.” Access the full list here. Xiologix is proud to have made this list with the additional distinction of being named as a “Pioneer 250”. Our networks are expanding and evolving faster than ever. The saying, “don’t fix what isn’t broken” doesn’t work in today’s technical environments. It is…
XDR Explained In 300 Words
Most XDR definitions are tedious & long. To give MSSPs clarity, Stellar Cyber VP Brian Stoner explains XDR security in 300 words. by Stellar Cyber • Jun 2, 2021 XDR is the rising star of new acronyms, but everyone wants you to read a 1,000+ word blog to understand its value. Let’s try to do it in about 300 words.Author: Brian Stoner, VP of service providers, Stellar CyberX means to expand DR’s – detection and response systems – to cover your entire attack surface, not just a portio…
